Wonderware Multi-Network Architecture Guide
.png?revision=1) |
|
| ARCHITECTURE GUIDE |
| Author |
Rufus Handsome |
| Publish Date | 07/28/2014 |
|
Applies to Software |
All Software |
|
Applies to Version |
ALL |
|
Applies to System/Module |
|
|
Article Version |
1.01.01 |
************************************************************************************************************************************************************
Summary
This article discusses the fundamental components of a multi-network architecture supporting a Wonderware based environment. It also provides an illustration of a working example of how a multi-network could be implemented to support a Wonderware environment. This article in no way advocates that this is the only way to implement a multi-network architecture, it is provided to show a fundamental example of how a typical multi-network architecture is laid out.
Overview
There are many ways to implement a network architecture but regardless of the implementation, a multi-network environment will utilize some form of network switches, routers, and possibly firewalls to protect the backend systems. Switches are used to concentrate the Ethernet connections coming from nodes such as PCs', PLC's, and Printers to a single point. Routers are used to "route" packets of data to network address destinations designated in the packets, similar to how the US Postal Service routes mail to homes in different neighborhoods based on the address. Firewalls help to protect the network from unwanted network traffic and intrusion.
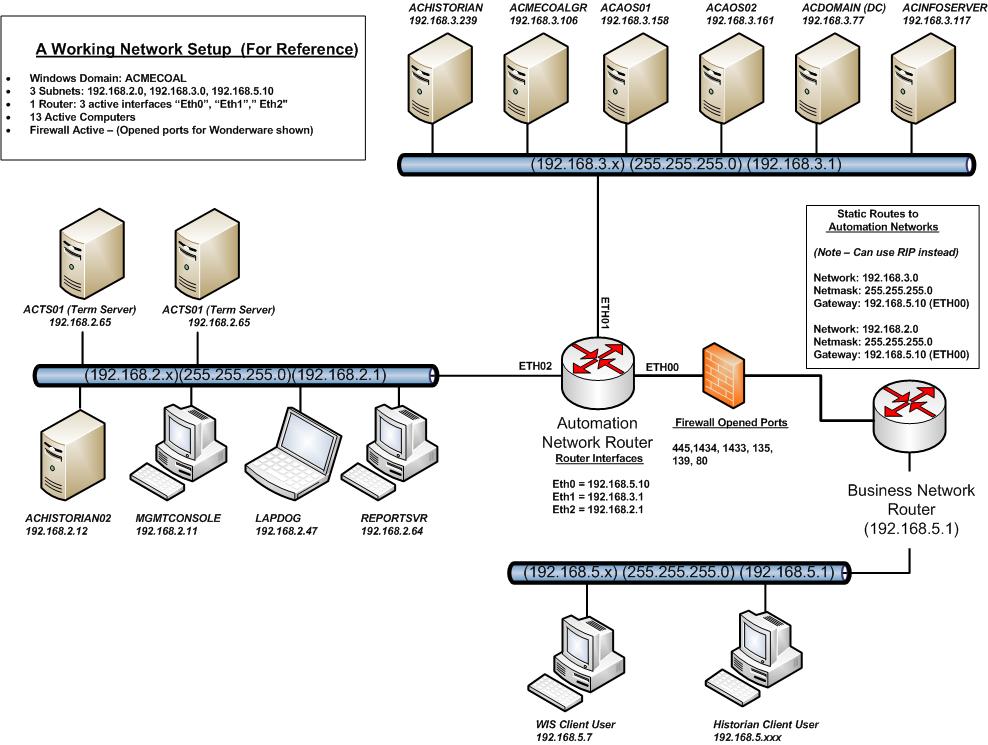
Multi-network architectures are often laid out in segments called subnets or "sub divided networks". Subnets can be segregated based on area, function, systems, or even security. For example in an industrial controls environment, there could be any combination of supervisory, PLC, administrative or business networks. Each network type would represent a segment in the overall network. As mentioned earlier, in order to connect these network segments together, a router is used to join all the network segments to a single point. In general, a router is configured to connect to each network via an interface port that will connect directly to a network segment's switch. Each interface port on the router is configured to be the "gateway" for a network segment. A properly configured router knows about the other networks and how to route packets between the networks to their destinations
When the router has been connected to all of the network segments, then each router interface is configured to be a gateway with the appropriate IP Address of that network segment, i.e., 192.168.3.1 means that the router is configured to be the gateway of 192.168.3.0 network. The router is traditionally designated to be the first node on a particular network, hence it is given .1 as it's last octet in it's IP Address, but this is not a rule.
Once systems on each network segment can successfully pass data packets between the networks (usually by "pinging" or using some other means of testing functionality), a firewall can then be put in place to further restrict the information flow to what is essential for normal day to day operations. Careful consideration should be observed as to where and how many firewalls should be placed in the network architecture, what type of security model will be followed, and what ports will need to be opened or closed for normal network operations and security.
Below are some common ports for a Wonderware based network that should be left opened:
For Historian and Application Servers
- 445/tcp -File and printer sharing
- 1434/udp -SQL Server Browser
- 1433/tcp -SQL TCP
- 135/tcp -DCOM
- 80/tcp - Information Server Web Portal
For Wonderware DAServers
1. 102 DAS SI Direct
2. 502 DAS MBTCP
3. 2221, 2222, 2223 DAS ABTCP
4. 5413 SuiteLiink DAServers
5. 44818 DAS ABCIP
Diagrams and Layout
Figure 1 Fundamental Network Layout Example